Microservice Interview -1
Question 1:
What is the API Gateway pattern?
Answer:
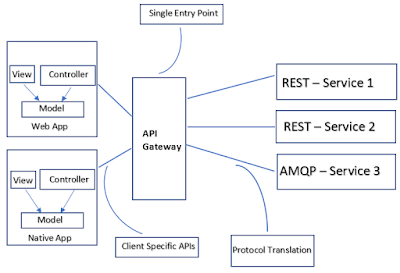
API Gateway is the entry point for all clients. The API Gateway handles requests in one of two ways:
Question 1:
What is the API Gateway pattern?
Answer:
API Gateway is the entry point for all clients. The API Gateway handles requests in one of two ways:
- Some requests are simply proxied/routed to the appropriate service.
- It handles other requests by fanning out to multiple services.
Rather than provide a one-size-fits-all style API, the API gateway can expose a different API for each client.
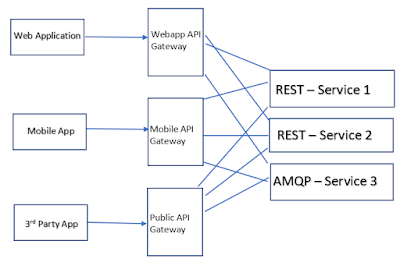
Variation : Backends for Frontends:
A variation of API Gateway pattern is the Backends for Frontends.
It defines a separate API Gateway for each kind of client.
In this example, there are 3 different types of APIs for 3 different types of clients.
Benefits of using API Gateway Pattern:
- Separates the clients from how the application is divided into microservices.
- Frees the clients from determining the location of microservices.
- Providing the optimal API for each client.
- It reduces the number of requests/round trips. e.g. : The API gateway enables the clients to retrieve data from multiple services with a single round-trip. Fewer round-trips means less requests from client and less overhead.
- Simplifies the client by moving the logic for calling multiple services from client to API Gateway.
Limitations of using API Gateway Pattern:
- Increased complexity: API Gateway needs to be developed, deployed and managed.
- Increased response time due to the additional network hop through the API Gateway.
Security using API Gateway's Access Token Pattern:
Problem: How to implement the identity of the requestor to the services that handle the request?
Solution:
The API Gateway authenticates the request and passes an access token [e.g. JSON Web Token] that securely identifies the requestor in each request to the services. A service can include the access token in requests it makes to other services.
This pattern has following benefits:
- The identity of the requestor is securely passed around the system.
- Services can verify that the requestor is authorized to perform the operation.



Please explain monolithic microservice architecture
ReplyDelete